MISC实验报告
实验一 LSB隐写的实现
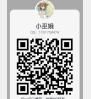
首先第一步,打开vaala的QQ,把vaala头像爬下来

爬下来是jpg,找个在线网站转成png
https://www.aconvert.com/cn/image/jpg-to-png/
这个就不错~
贴代码:
from PIL import Image as im
import re
replace_reg = re.compile(r'[1|0]$')
# 替换最后一位的数据,source是被替换数据,target是目标数据,就是batarget放到source最后一位
def repLstBit(source, target):
return replace_reg.sub(target, source)
# 运行结果:'123X'
print(repLstBit("111110", "1"))
# 字符串转换二进制,不够八位的话补齐8位
def encode(s):
return ''.join(bin(ord(c)).replace('0b', '').rjust(8, '0') for c in s)
# 切割从图像中收集到的数据,就是把载密图像的对应最后一位提取出来之后需要进行切割
def cut_text(text, lenth):
textArr = re.findall('.{' + str(lenth) + '}', text)
tempStr = text[(len(textArr) * lenth):]
if len(tempStr) != 0:
textArr.append(text[(len(textArr) * lenth):])
return textArr
# 二进制转换成字符串,看上面切割方法的注释即可理解该方法存在的意义
def decode(s):
bitArr = cut_text(s, 8)
return "".join(chr(int(i, 2)) for i in bitArr)
# 读取宿主图像和要写入的信息生成载密图像。
if __name__ == '__main__':
img = im.open("D:\\f盘\\python\\pycharm\\222\\1.png")
width = img.size[0]
height = img.size[1]
hideInfo = "vaalacat yyds"
hideBitArr = encode(hideInfo)
count = 0
bitInfoLen = len(hideBitArr)
print(hideBitArr)
for i in range(width):
for j in range(height):
if count == bitInfoLen:
break;
pixel = img.getpixel((i, j));
print(pixel[0])
sourceBit = bin(pixel[0])[2:]
print(sourceBit)
rspBit = int(repLstBit(sourceBit, hideBitArr[count]), 2)
count += 1
img.putpixel((i, j), (rspBit, rspBit, rspBit))
img.save("D:\\f盘\\python\\pycharm\\222\\2.png")
1.png是原图,2.png是生成的加密图片~

使用Stegsolve处理图片

打开vaalacat


vaalacat yyds
实验二 压缩包分析
使用winhex打开康康~
[CTF]zip伪加密_林毅洋的博客-CSDN博客_ctf zip伪加密

伪加密,但我第一次找错位置了,不该改上面的位置~(:з」∠)

应该把这个1改成0

就能解压了
解压以后出来新的压缩包,继续用winhex康康

奇数,真加密了,爆破叭~(:з」∠)


当我使用不同的软件爆破了n次以后(里面压缩包套压缩包),我死了,决定写python脚本了~
import os
import zipfile
#dir = "C:\\Users\\brighten\\Desktop\\ff\\"
dir = "D:\\f盘\\python\\pycharm\\222\\666\\"
l=[...]
# for line in passFile.readlines():
n = 0
s2 = ""
def jieya():
i = "2.zip"
p = '1'
for x in range(10000):
ss = i[:i.find(".")]
print(i)
zpf = zipfile.ZipFile(dir + ss + ".zip")
list = zpf.namelist() # 得到压缩包里所有文件
for f in list:
for line in l:
try:
password = line.strip('\n')
# srcfile.extractall(path='C:\\Users\\Administrator\\Desktop\\', members=zfile.namelist(),
zpf.extract(f, dir, password.encode('utf-8'))
if zpf.extract(f, dir, password.encode('utf-8')):
print(password.encode('utf-8'))
break
except:
pass
#zpf.extract(f, dir, ss.encode('utf-8')) # 循环解压文件到指定目录,密码
print(ss + "解压成功" + str(f))
zpf.close()
os.remove(p+".zip")
p=ss
print(x)
i = str(f)
#这里注释掉的代码是一个字典,记录重复的文件名,没有用
'''t = {}
for i in range(10000):
s = str(i)
while len(s) < 4:
s = '0' + s
t[s] = False'''
jieya()
l[…]是字典,太长了不写了,本来以为是读文件太慢所以塞到列表里了,后来发现其实还是爆破太慢~
s=''
s1=''
for a in range(10):
for b in range(10):
for c in range(10):
for d in range(10):
s=s+str(a)+str(b)+str(c)+str(d)
#print(s)
s1 = s1 + "'" + s + "'" + ','
s=''
print(s1)
以上是字典生成算法

3s爆破一层,碎觉的时候开始挖矿~

睡醒了就爆破好啦,还不到1000层~

flag{6pLYbihLkXKUIeZqMt59ET5LKrxg9N}
PS:给瑶瑶准备了一份代码,正式提交的时候会删除(。・・。)ノ♡
import os
import zipfile
import base64
dir = "D:\\f盘\\python\\pycharm\\222\\666\\"
n = 0
i = "NzI2NQ==.zip"
for x in range(10000):
ss = i[:i.find(".")]
print(i)
zpf = zipfile.ZipFile(dir + ss + ".zip")
list = zpf.namelist() # 得到压缩包里所有文件
for f in list:
zpf.extract(f, dir, base64.b64decode(ss)) # 循环解压文件到指定目录,密码
print(ss + "解压成功" + str(f))
zpf.close()
os.remove(ss + ".zip")
print(x)
i = str(f)
实际上压缩包密码是文件名的base64反编,代码里的 i 填写压缩包的名字~(:з」∠)

实验三 键盘流量分析
wireshark打开流量包

协议是usb端口的,题干也说明了是键盘流量分析
就是有垃圾杂包
usb.src == “1.6.2”
把有用的包筛选出来,然后
文件 》导出特殊分组 》保存为 2.pcapng

cmd先进入wireshark安装目录,把2.pcapng也放进去(懒得配环境变量
tshark -r 2.pcapng -T fields -e usb.capdata > usbdata.txt


然鹅我的和别人的长得不一样呜呜呜~

垃圾wireshark,一会就把它删掉~

还要调格式
f=open('usbdata.txt','r')
fi=open('out.txt','w')
while 1:
a=f.readline().strip()
if a:
if len(a)==16: # 鼠标流量的话len改为8
out=''
for i in range(0,len(a),2):
if i+2 != len(a):
out+=a[i]+a[i+1]+":"
else:
out+=a[i]+a[i+1]
fi.write(out)
fi.write('\n')
else:
break
fi.close()

调完格式就能抄脚本了_(:з」∠)_
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t",
"2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\",
"32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".",
"38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>",
"3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>",
"44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>",
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"",
"34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>",
"3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>",
"41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('out.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))

已经做到底了,完结撒花~(。・・。)ノ♡